Cyber resiliency is the bedrock of an organization’s ability to withstand cyberattacks. A CISO’s role is pivotal in crafting and implementing effective cyber resiliency programs. In its recent Executive Summary Report, Datos Insights delves into the principles behind developing a robust cyber resiliency strategy. Some key findings of the report include:
- Organizations confuse cyber resiliency with cybersecurity: Cybersecurity is focused on detecting and preventing cyberattacks. Cyber resiliency is the ability to mitigate damage and recover from an attack.
- Organizations separate cyber and infrastructure resiliency: Digital and physical components of an IT estate are inexorably connected; however, they’re often siloed in resiliency planning.
- Organizations underestimate the codependency of cybersecurity and business continuity: Business continuity and cybersecurity are intricately linked, each playing a crucial role in an organization’s resilience.
Arguably, cyberattacks are a top threat to business continuity. Impacts to organizations are rarely isolated departmental events but rather widespread, requiring a holistic approach to resiliency planning. However, organizations silo business continuity and cybersecurity functions relegating them to fall short of their prime objectives. Cyberattacks rarely affect only IT infrastructure; the impacts ripple through an organization.
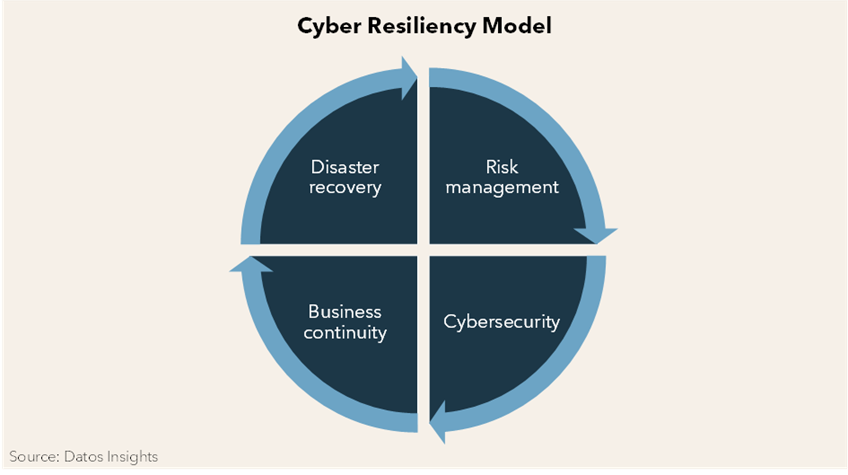
Cyber Resiliency Model
There are four interrelated quadrants of the cyber resiliency model. The first quadrant, risk management, seeks to identify all risks by all causes. Quadrant two, cybersecurity, which is well known to CISOs, is generally not interconnected to quadrants three and four. This disconnect is where achieving cyber resiliency stalls.
Quadrant three concerns the organization’s ability to maintain operations and deliver critical services. Quadrant four restores damaged or altered IT infrastructure. CISOs typically do not work in the cyber resiliency model’s business continuity and disaster recovery quadrants.
The figure below illustrates a cyber resiliency program’s four inexorably linked components.
A cyber security solution protects digital assets from attacks, while cyber resiliency limits the damage, downtime, service disruptions, and financial losses cyberattacks cause. Datos Insights believes that the next IT chapter must be cyber resiliency engineering, where all quadrants of the cyber resiliency model are instantiated. CISOs must remove the walls that create barriers to an integrated approach to surviving today’s complex hydra cyberattacks.
Final Thoughts
CISOs must share the mantle of business continuity to ensure a resilient organization regardless of the egregiousness of an attack. To learn more about cyber resiliency, check out my report entitled, CISO Guide to Cyber Resiliency: Building a Future of IT Stability. I would love to hear how you have melded cybersecurity with cyber resiliency; drop me a line here to share your thoughts. If you want to keep up with my blogs on related IT security issues, go here.