It is reported that the average number of APIs organizations use can range from 15,564 to 25,592. According to F5, there could be 1.7 billion APIs in use by 2030, making APIs one of the largest known software components of an enterprise attack surface. Hackers increasingly target APIs as the gateway to an organization’s sensitive information.
A 2022 Salt Security report states that 94% of companies experienced security problems in production APIs, and 20% have experienced a breach resulting from an insecure API. The growing threat introduced by such widespread API use is one of the reasons Aite-Novarica Group ranked API security second in its Top 10 Trends in Cybersecurity, 2023: A Sea of Change for the Industry report.
Brief History of API Security Products
An increasing number of API exploits and attacks drove the development of purpose-built API security products. The API security product market as we know it today emerged from 2013 to 2014 when vendors such as Cequence Security, Curity, ThreatX, and Wallarm launched products designed to secure APIs.
Over the next eight years, dozens of products claiming to secure APIs flooded the market. Eighty vendors now crowd the market, vying for a share of the CISOs’ wallets in securing APIs.
What Is API Security?
API security is the application of practices, policies, and products that detect, prevent, and mitigate attacks targeting APIs. Today’s pervasive use of APIs requires a concerted effort to protect one of the most vital and vulnerable aspects of an information technology’s attack surface. Protecting APIs has created a rapidly growing market of products and services designed to protect APIs, but protecting APIs is easier said than done.
The first step requires understanding the types of APIs an organization uses and how APIs are consumed. Public, private, and partner types of APIs all require a unique approach to security. The need for understanding doesn’t end there; organizations must also know the API protocols to determine the best security architecture and runtime controls to apply.
The API ecosystem section of this report discusses API types and protocols in more depth. Protecting APIs requires a partnership with application development that understands how APIs work, enterprise architects who understand the various protocols, and security engineers who can apply the necessary security controls.
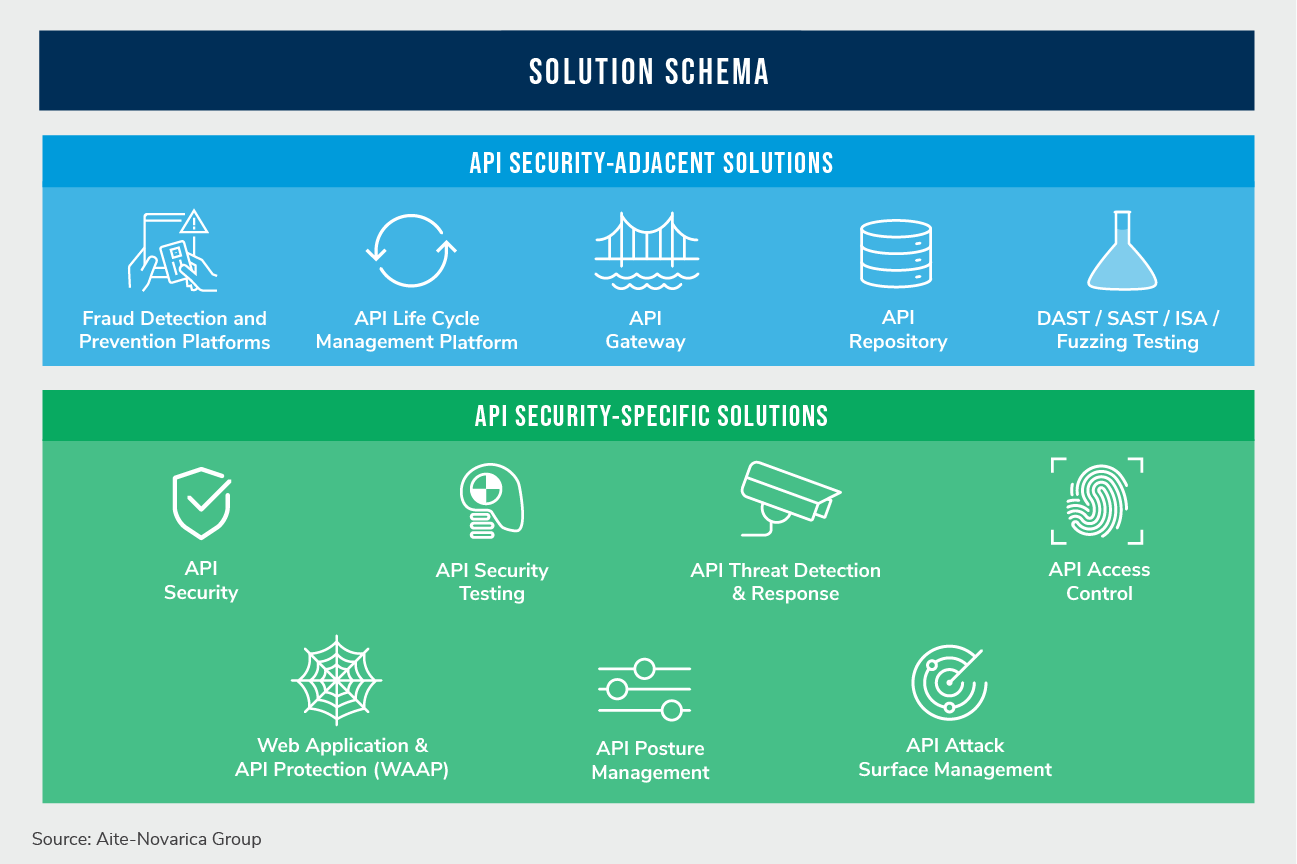
API Schema
Today, 80 API security solutions target a niche or a broad spectrum of API threats and vulnerabilities. So many that Aite-Novarica Group had to create a product schema to keep them all straight. The schema has two planes: One is API security-adjacent solutions, and the second is API security-specific solutions. Twelve categories of solutions exist among the two planes.
API security-adjacent solutions are products originally designed for purposes other than security; however, they evolved to include one or more security functions to protect APIs. Security-specific solutions are products designed to solve one or more API security problems.
The figure below is the API security schema.
Final Word
If you are confused about the plethora of API security options available to you, check out my latest report entitled API Security: Market Landscape. This report provides a brief history of API security, the market size, a discussion about the API ecosystem, an API security model, vendors offering products aligned to the schema, and much more.