June 21, 2021 – Passwords are the most dangerous contributing factor in cyberattacks. Many financial institutions are revising their identity and access management frameworks to omit the use of passwords. The convergence of technology, end-user familiarity, and corporate infrastructures dependent on security assertions markup language and active directory make passwordless authentication a practical solution for organizations.
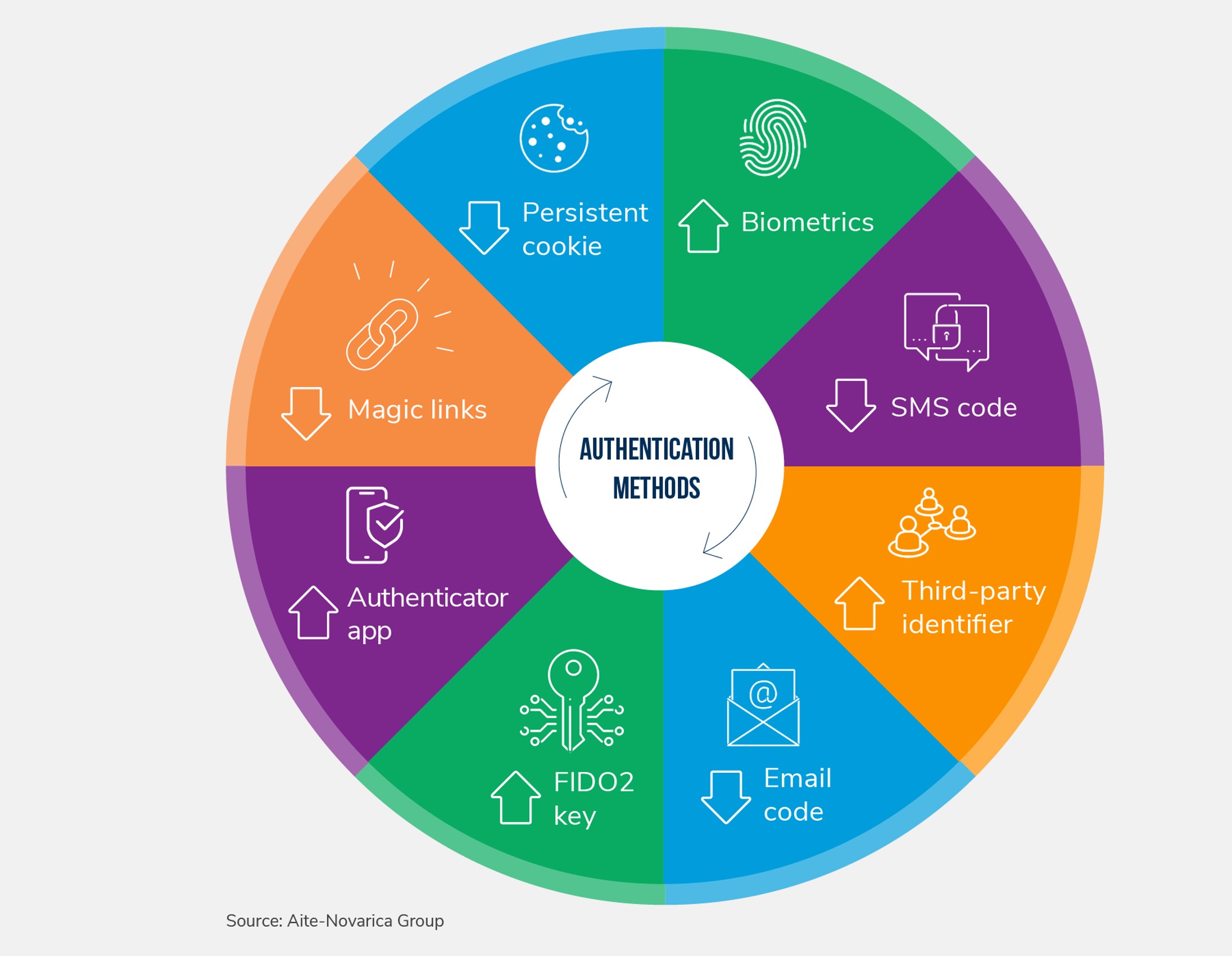
This Impact Report explores the key trends within the passwordless authentication market and discusses how technology is evolving to address market needs and challenges. It is based on interviews, surveys, and demonstrations of several key providers of passwordless authentication solutions, as well as an analysis of 38 passwordless authentication vendors.
This 31-page Impact Report contains seven figures and four tables. Clients of Aite-Novarica Group’s Cybersecurity service can download this report and the corresponding charts.
This report mentions 1Kosmos, 12iD, Acceptto, Authentiq, Axiad, Beyond Identiy, Cisco Systems, Cotter, Duo, Entrust, FIDO Alliance, Francisco Partners, FushionAuth, GateKeeper Proximity, Govest Inc., HYPR, Identité, Iovation, JPMorgan Chase, Keyless Technologies Inc., LastPass, LaunchKey MFA, LogMeIn, Magic Labs Inc., Microsoft, National Institute of Standards and Technology, Nok Nok Labs Inc., OneLogin, Okta, Ping Identy, Prove Identity Inc., Pure ID, Sawo Labs, Secret Double Octopus, SecureAuth, Stych Inc., Swoop In Technologies, Thales Group, Transmit Security Inc., TransUnion, Trusona, TruU, Veridium, Verizon, Widas ID GmbH, World Wide Web Consortium, XignSys GmbH, and Yubica Inc.