The short answer is yes. With cyber ranges, there is no longer an excuse to undertrain frontline cybersecurity personnel. Cybersecurity should follow the example of FAA pilot training requirements: Commercial pilots must have 1,500 real-world flight hours and 100 in a simulator replicating difficult operational conditions. I would guess that no CISO would step on a plane without a pilot undergoing advanced simulator training.
Cyber ranges are changing the landscape of cybersecurity education. Cyber range solutions provide an effective method of upskilling cybersecurity personnel: Classroom training is limited in teaching critical cybersecurity defensive techniques. Adding the training dimension of gamification and live-fire ranges to defensive cybersecurity training increases knowledge retention and builds reactive event muscle memory. Certification courses have limitations in practically applying curricula. Cyber ranges offer live cyberattack training with a virtually limitless library of defense scenarios. Cyber ranges push past the theoretical to the practical.
Cyber ranges are available for organizations and budgets of all sizes: The cyber range market comprises nearly 60 solution providers offering large in-house platform deployments to cloud service models. Ranges are available for any size, budget, skill level, and training requirements, with a limitless library of defense scenarios. Cyber ranges push past the theoretical to the practical.
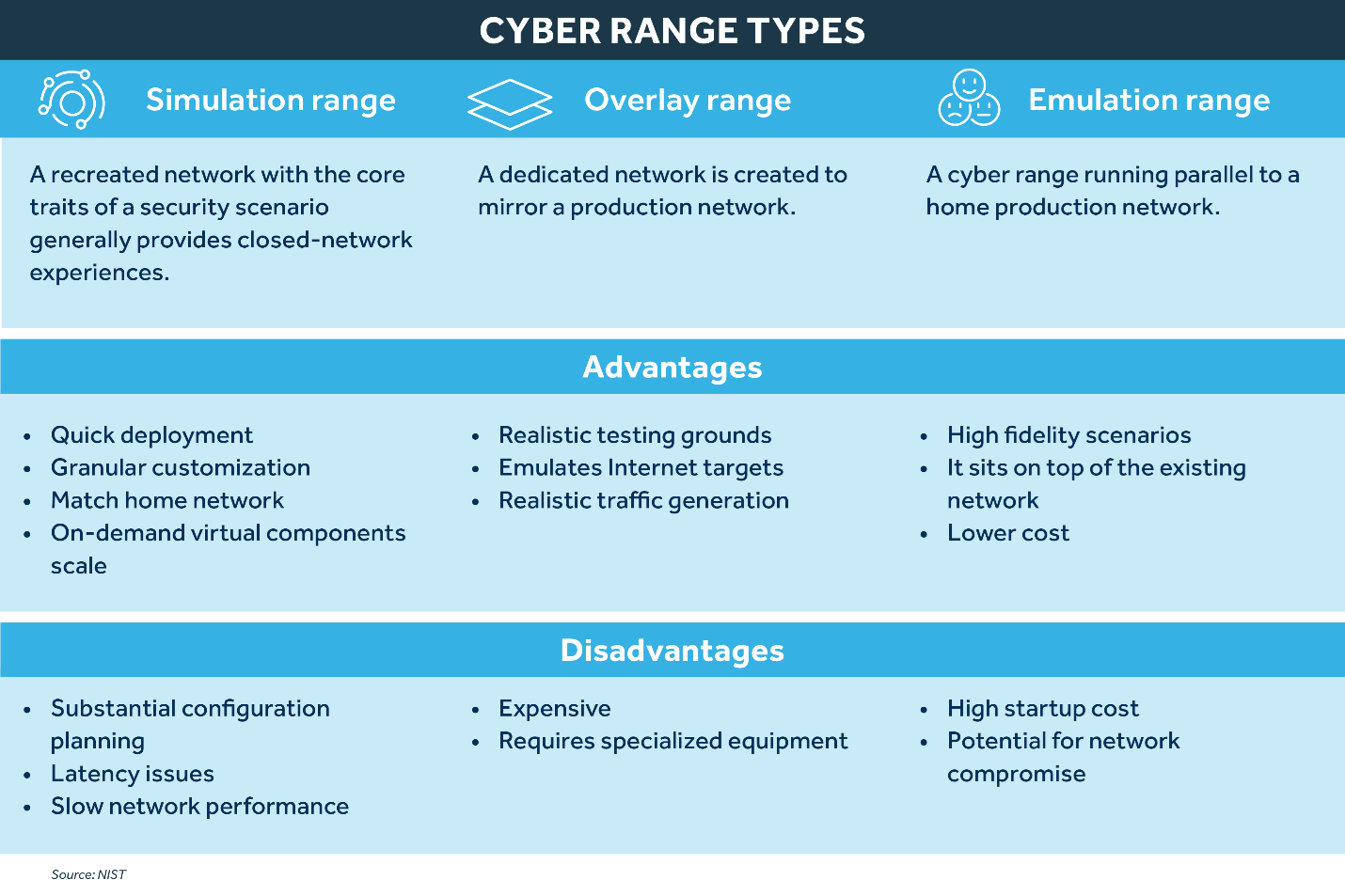
Cyber ranges are interactive simulated platforms replicating home networks, systems, tools, and other components. Several types exist owing to the diversity of organizations’ testing preferences:
- Simulation range: These cyber ranges simulate real-world scenarios and are used to train cybersecurity professionals to respond to various cyber threats. They are designed to be as realistic as possible and can be customized to meet specific training needs.
- Overlay range: Overlays simulate cyberattacks on existing networks and systems. They are designed to test the effectiveness of security measures and identify vulnerabilities in the system.
- Emulation range: Emulations create virtual environments that mimic real-world networks and systems. These types of cyber ranges are used to test the performance of security measures and identify potential vulnerabilities in the system.
- Hybrid range: Hybrid cyber ranges combine elements of simulations, overlays, and emulations to create a comprehensive training environment. They are designed to provide cybersecurity professionals with a more realistic and immersive training experience.
Information security training programs without a cyber range will find themselves ill-equipped to combat emerging threats.
Final Thoughts
To learn more about cyber ranges, check out the blog, Is There a Difference Between Breach and Attack Simulation and Cyber Range Platforms? I would love to hear how you have leveraged cyber ranges to improve training; drop me a line here to share your thoughts. If you want to keep up with my blogs on related IT security issues, go here.