Boston, August 5, 2021 –Sitting back and waiting to detect indicators of compromise is no longer the most effective strategy to ward off bad actors. Some organizations have gone on seek-and-destroy missions to hunt down bad actors and malicious insiders, seeking evidence of or stopping their malicious activity. Threat hunting leverages cyber intelligence, threat analytics, security information, event management solutions, and threat hunter tradecraft to hunt advisories. Threat hunting finds threats otherwise missed by conventional security technologies.
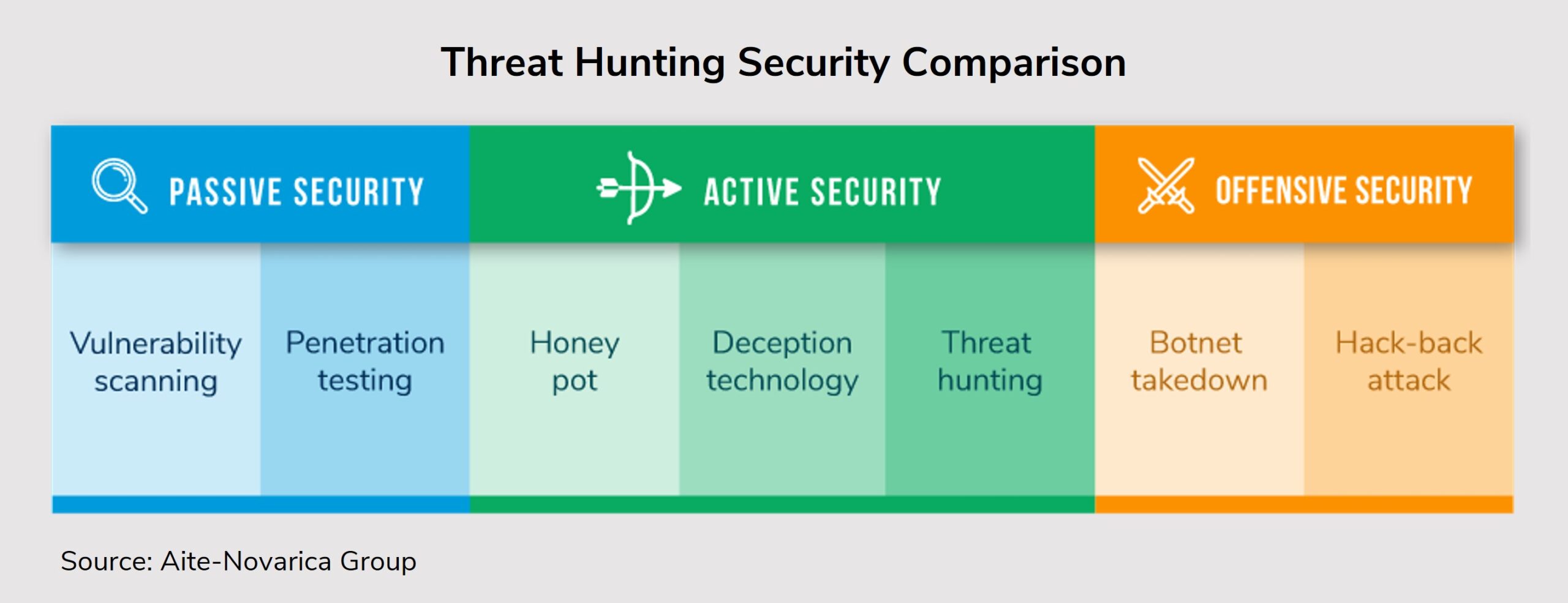
This Impact Report targets security operations departments looking to adopt an offensive information security approach and provides valuable insight to both buyers and sellers of threat hunting products and services. This report is based on Aite-Novarica Group’s review of industry publications, white papers, and over 200 vendor websites to identify a cross-section of threat hunting vendors. Aite-Novarica Group selected 104 vendors to further analyze and understand the general threat hunting market.
This 92-page Impact Report contains seven figures and 12 tables. Clients of Aite-Novarica Group’s Cybersecurity service can download this report, the corresponding charts, and the Executive Impact Deck.
This report mentions Alphabet, ATOS, Bessemer Venture Partners, Capgemini, Capital G, Colgate, CrowdStrike, Crowe, Cyber Mentor Fund, Cybereason, Cyborg Security Inc., Delta Airlines, Devo Inc., Elbit Systems Inc., eLearn Security, eSentire, Expel Inc., FedEx, Fortified Health, Georgian, GreenSky, Henry Schein, Hogan Lovells, HYAS, IBM Security, Information Assurance Certification Review Board, Insight Partners, Kognos, Lockheed Martin, Lucas Venture Group, M12, Mandiant, Microsoft, MITRE, Mondelez, Mossé Cyber Security Institute, Providence Strategic Growth, PwC, S3 Ventures, SANS Institute, Securaa.io, Siemplify, SolarWinds, Swimlane, Talent.com, ThreatConnect, ThreatQuotient, VMware CarbonBlack, Warburg Pincus, Wesley Clover, and ZipRecruiter.